About USB attacks
In a previous installment, we covered the dangers posed by USB attacks, in particular HID emulation attacks (à la Rubber Ducky), and some of the techniques we can use to mitigate the risks (spoiler: defense does not always have to be high-tech).
On Linux systems, we can use USBGuard as a USB “firewall”, to safe-list USB equipment based on their hardware characteristics (Vendor ID, product ID, device class etc).
We can also use Wazuh as a SIEM to monitor USB events on workstations, and detect previously unknown equipment being plugged in to our systems.
On a Linux computer the output of the lsusb command looks like this:
Bus 001 Device 001: ID 1d6b:0002 Linux Foundation 2.0 root hub Bus 001 Device 002: ID 046d:c32c Logitech, Inc. Keyboard K120 Bus 001 Device 003: ID 0e8f:0031 GreenAsia Inc. Multimedia Keyboard Controller Bus 001 Device 004: ID 058f:6314 Alcor Micro Corp. AU6477 Card Reader Controller Bus 001 Device 005: ID 046d:c050 Logitech, Inc. RX 250 Optical Mouse Bus 002 Device 001: ID 1d6b:0003 Linux Foundation 3.0 root hub Bus 003 Device 001: ID 1d6b:0002 Linux Foundation 2.0 root hub Bus 004 Device 001: ID 1d6b:0003 Linux Foundation 3.0 root hub
This gives us an overview of currently plugged-in devices, description and manufacturer along with vendor ID and product ID. Many USB devices also have serial numbers (use lsusb -v for details). All those characteristics can be used to filter (or report) unwanted USB devices.
Rogue devices such as the Rubber Ducky and its variants use hardcoded or randomized identification strings. So, in theory we can detect and interdict USB devices we do not recognize.
But what if we could clone the identification strings of legitimate equipment?
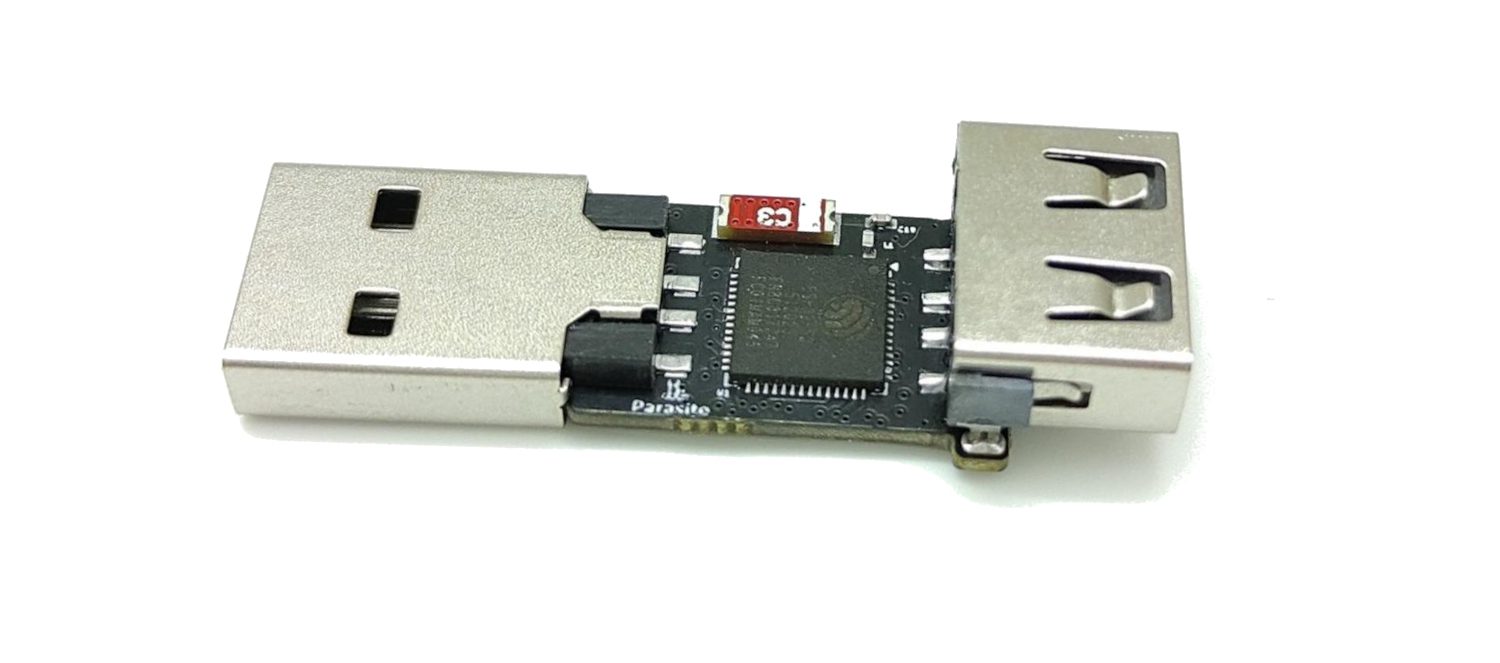
This is exactly what the newly-released Diabolic Parasite device does.
Designed by a cybersecurity outfit from Egypt, this hardware implant can be seen as an evolution of the well-established Rubber Ducky. Rather than present itself as a generic keyboard with its own identification strings, it is able to clone the characteristics of a regular USB device, such as a keyboard or a mouse – simply by plugging it between a computer USB port and the USB device you want to clone.
Thus, it behaves as a man in the middle, that can perform keystroke injection by impersonating the legitimate equipment. It also acts as a key logger and can be remote-controlled over wifi.
This makes the attack more stealth, leaving fewer traces. The operating system does not notice any change, so we avoid pop-up notifications about new hardware being found.
Features:
- USB Type-A input
- on-board wifi for remote access
- LED for status indication
The Diabolic Parasite is currently on sale on CrowdSupply (disclaimer: we are not affiliated with the vendor but intend to order our own sample).
If you are doing physical intrusion tests, then the Diabolic Parasite should be a worthy addition to your toolbox.
Conclusion
Defeating USB attacks requires effort, because they are easy to carry out and difficult to detect. At the same time, hardening computers against USB attacks has become more difficult, in light of novel attack techniques.
More than ever, this demonstrates that there is no computer security without physical security.
Securing workstations is essential, and good security hygiene means not leaving workstations unattended and unlocked in unsafe environments.
Distraction can be fatal – after all, keystroke injection attacks take just a few seconds to execute, and they have become even more stealth.
References